This tutorial covers the four most commonly used core actions:
core.transform.reshape, core.http_request, core.http_poll, and core.script.run_python.To learn about the other core actions, check out the following tutorials:core namespace.
They are distinct from pre-built integrations in the tools namespace, which are pre-configured for specific 3rd-party tools.
There are five sub-namespaces under core:
corecore.transformcore.workflowcore.requirecore.script
core actions are the most commonly used actions in Tracecat.
They include:
| Name | Display Name | Description |
|---|---|---|
core.transform.reshape | Reshape | Reshape and manipulate data. |
core.transform.scatter | Scatter | Split a list of data into individual items. |
core.transform.gather | Gather | Merge scattered data back into a single list. |
core.http_request | HTTP Request | Make a HTTP request. |
core.http_poll | HTTP Polling | Poll a REST API until a condition is met. |
core.grpc_request | gRPC request | Call a gRPC method using an inline proto definition. |
core.script.run_python | Run Python script | Execute custom Python code in a secure sandbox. |
Reshape
Reshape is a simple action that takes a single inputvalue (e.g. a string, number, or object),
evaluates any expressions and functions, and returns the result.
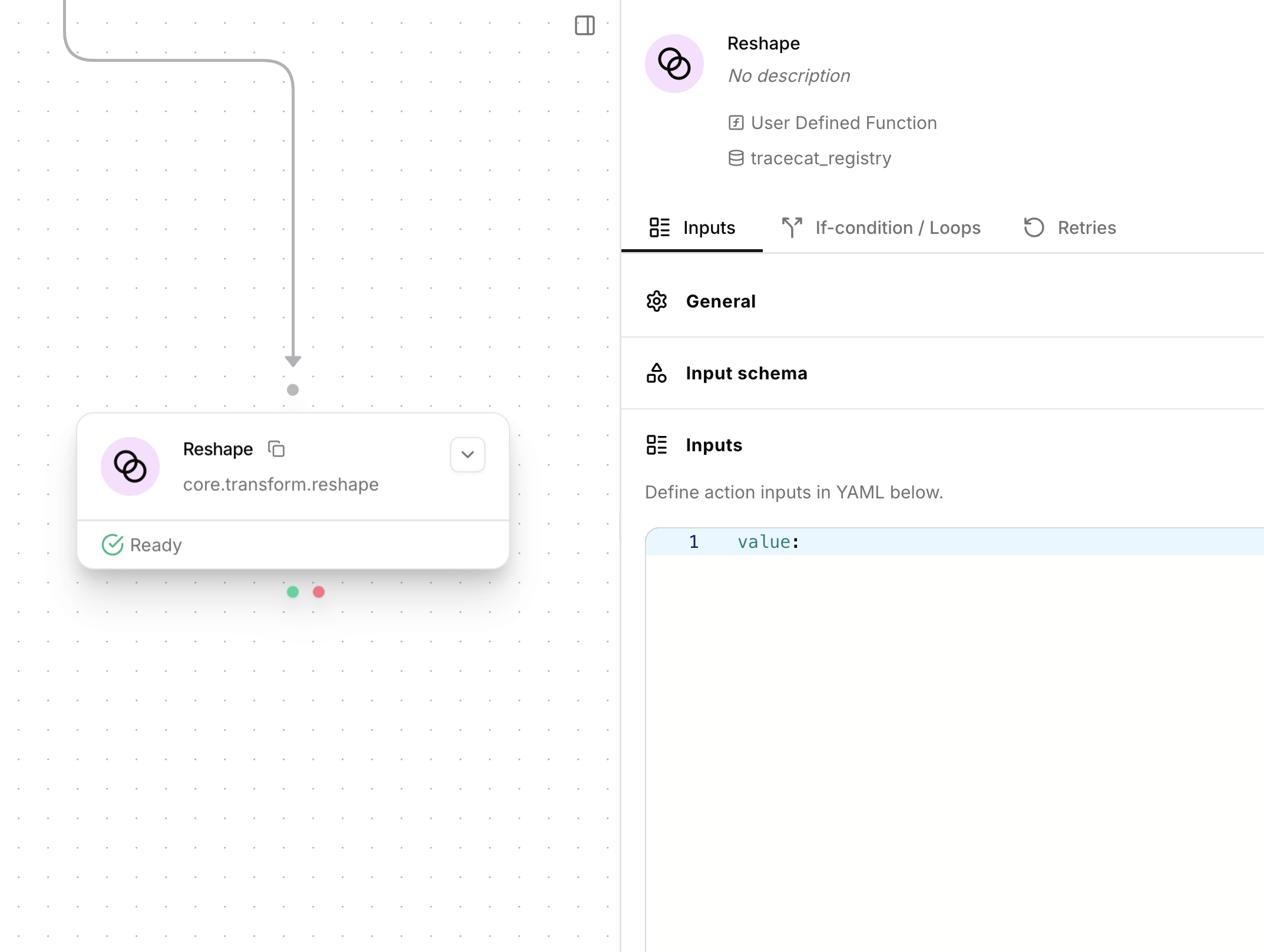
Reshape action.
HTTP Request
Perform an HTTP request to a given URL. Parametersurl(HttpUrl, required): The destination of the HTTP request.method(Literal[“GET”, “POST”, “PUT”, “PATCH”, “DELETE”], required): HTTP request method.headers(dict[str, str], optional): HTTP request headers.params(dict[str, Any], optional): URL query parameters.payload(dict[str, Any] | list[Any], optional): JSON serializable data in request body (POST, PUT, and PATCH).form_data(dict[str, Any], optional): Form encoded data in request body (POST, PUT, and PATCH).files(dict[str, str | FileUploadData], optional): Files to upload using multipart/form-data.- The dictionary key is the form field name for the file (e.g.,
"file","attachment1"). - The value can be:
- A simple base64 encoded string representing the file content. In this case, the
form_field_namewill also be used as the filename in theContent-Dispositionheader. - A dictionary (
FileUploadData) with the following keys:filename(str): The actual filename to be sent in theContent-Dispositionheader (e.g.,"mydocument.pdf"). If not provided or empty, theform_field_namewill be used.content_base64(str, required): The base64 encoded string of the file content.content_type(str, optional): The MIME type of the file (e.g.,"application/pdf","image/png"). If not provided,httpxwill attempt to guess it.
- A simple base64 encoded string representing the file content. In this case, the
- The dictionary key is the form field name for the file (e.g.,
auth(dict[str, str], optional): Basic auth credentials withusernameandpasswordkeys.timeout(float, optional, default: 10.0): Timeout in seconds.follow_redirects(bool, optional, default: False): Follow HTTP redirects.max_redirects(int, optional, default: 20): Maximum number of redirects.verify_ssl(bool, optional, default: True): Verify SSL certificates.
HTTP TLS and CA setup
You can attach a client certificate (mTLS) and/or a custom CA bundle tocore.http_request and core.http_poll by creating workspace secrets with
specific names and keys.
Create these secrets in the workspace credentials UI:
mtls(type:mtls)TLS_CERTIFICATE: PEM-encoded certificate (chain ok)TLS_PRIVATE_KEY: PEM-encoded private key
ca_cert(type:ca-cert, optional)CA_CERTIFICATE: PEM-encoded CA bundle
verify_ssl: false
to disable verification entirely; otherwise a provided ca_cert overrides the
default CA bundle.
File Upload Examples (files parameter):
-
Simple Base64 Upload (filename defaults to form field name):
-
Upload with Custom Filename and Content Type (using
FileUploadDatadict): -
Multiple File Uploads (mixed simple and detailed):
HTTPResponse (dict):
status_code(int)headers(dict)data(str | dict | list | None)
HTTP Polling
Perform an HTTP request to a given URL with polling. Parameters- Accepts all parameters from
core.http_requestexcept for thefilesparameter.core.http_polldoes not support file uploads. poll_retry_codes(int | list[int], optional): Status codes on which the action will retry. If not specified,poll_conditionmust be provided.poll_interval(float, optional): Interval in seconds between polling attempts. If not specified, defaults to polling with exponential wait.poll_max_attempts(int, optional, default: 10): Maximum number of polling attempts. If set to 0, the action will poll indefinitely (until timeout).poll_condition(str, optional): User defined Python lambda function. When it returns a truthy value, stops polling. If not specified,poll_retry_codesmust be provided.
HTTPResponse (dict) - same as core.http_request.
Poll condition
Thepoll_condition parameter is a Python lambda function string that determines whether to retry.
The function receives a dict with headers, data, and status_code fields.
The function should return True if the polling should stop, and False if the polling should continue.
Examples:
HTTP Paginate
Paginate through a HTTP response. Parameters- Accepts all parameters from
core.http_requestexcept for thefilesparameter.core.http_paginatedoes not support file uploads. stop_condition(str, required): User defined Python lambda function. When it returns a truthy value, stops pagination.next_request(str, required): User defined Python lambda function. Returns the next request as a JSON ofurl,method,headers,params,payload,form_datato paginate to.items_jsonpath(str, optional): JSONPath expression that evaluates to the items to paginate through.limit(int, optional, default: 1000): Maximum number of items to paginate through.
- With
items_jsonpath: A flat list of items collected across pages, truncated tolimititems. - Without
items_jsonpath: A list of per-pageHTTPResponseobjects, wherelimitapplies per page.
To capture the entire response body from each page as items, set
items_jsonpath to $.
This returns a flat list of page bodies (e.g., [page1_body, page2_body, ...]).
If you omit items_jsonpath, the action returns a list of full HTTPResponse objects (headers, status_code, data) — one per page.gRPC Request
Call a gRPC method using an inline proto definition. Parameterstarget(str, required): gRPC server address inhost:portformat.service_name(str, required): gRPC service name (e.g.,"API").method_name(str, required): gRPC method name (e.g.,"Query").request_message_name(str, required): Request message type name (e.g.,"VQLCollectorArgs").proto(str, required): Inline.protodefinition. File paths are not supported.request_payload(dict[str, Any], optional): Request payload as a dict matching the protobuf schema.timeout_seconds(float, optional): Timeout in seconds for the RPC. Defaults to no timeout.insecure(bool, optional, default: False): Use an insecure plaintext channel.channel_options(dict[str, str | int], optional): gRPC channel options (e.g.,{"grpc.ssl_target_name_override": "service.local"}).ssl_target_name_override(str, optional): TLS target name override for self-signed certificates.
- Unary RPCs return a dict representation of the response message.
- Server-streaming RPCs return a list of response dicts.
gRPC TLS and CA setup
You can attach a client certificate (mTLS) and/or a custom CA bundle tocore.grpc_request by creating workspace secrets with specific names and keys.
Create these secrets in the workspace credentials UI:
grpc_mtls(type:mtls)TLS_CERTIFICATE: PEM-encoded certificate (chain ok)TLS_PRIVATE_KEY: PEM-encoded private key
grpc_ca_cert(type:ca-cert, optional)CA_CERTIFICATE: PEM-encoded CA bundle
insecure: true to disable TLS entirely.
Example:
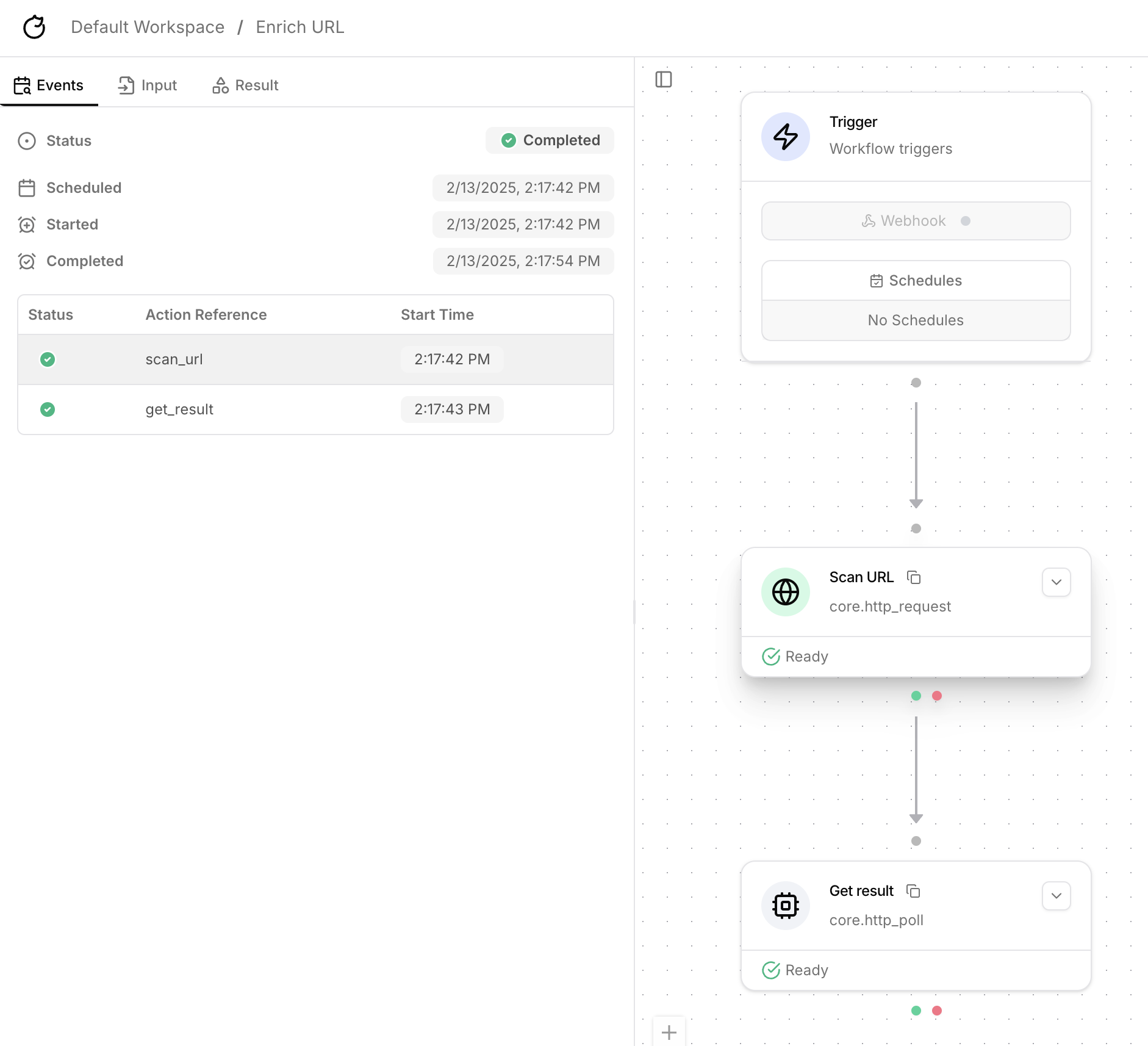
Tutorial: URLScan
URLScan uses a two-step process to get a threat intelligence report on a URL:- Call the
/scanendpoint to submit the URL for scanning. - Poll the
/resultendpoint repeatedly until the status code changes from404to200. - Uses a reshape to extract the maliciousness score and categories from the response body.
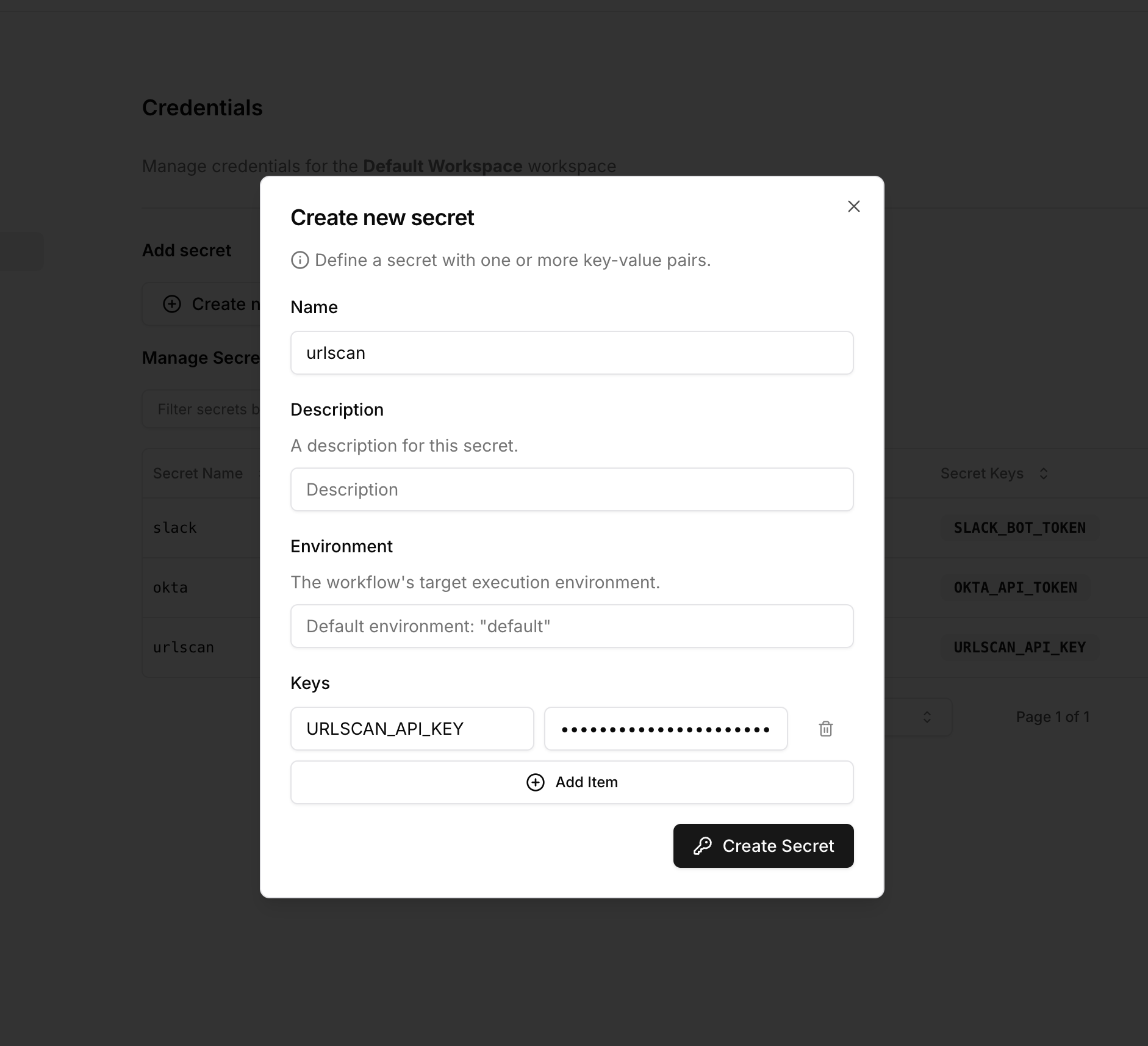
Create URLScan secret
Add URLScan API key to Tracecat’s built-in secrets manager.
- Open credentials settings
- Create secret
Select the settings icon in the top right corner of the page and click on 
Credentials.
Call /scan endpoint
Add the 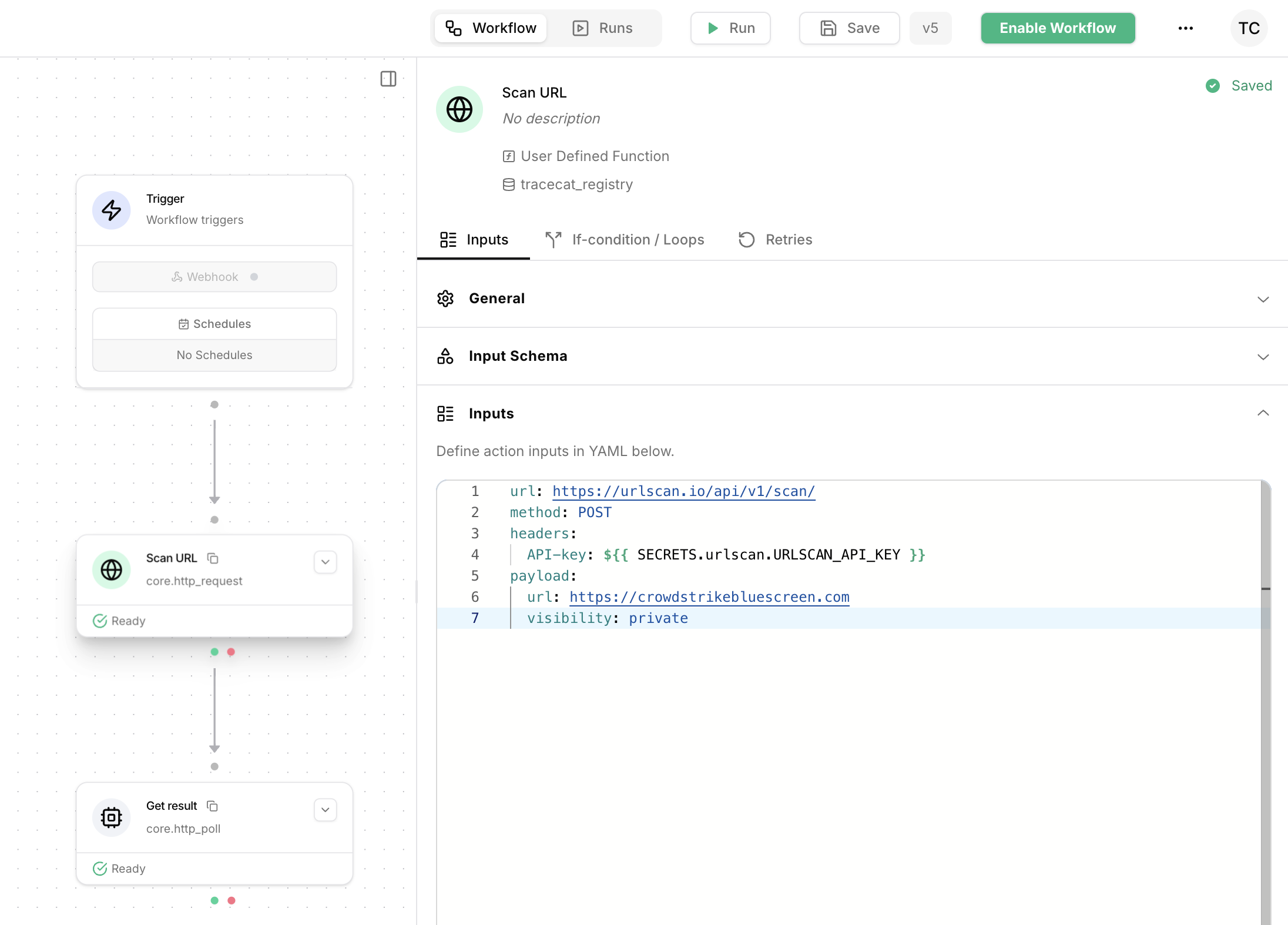
core.http_request action to your workflow.
Rename it to Submit URL and configure it with the following inputs:
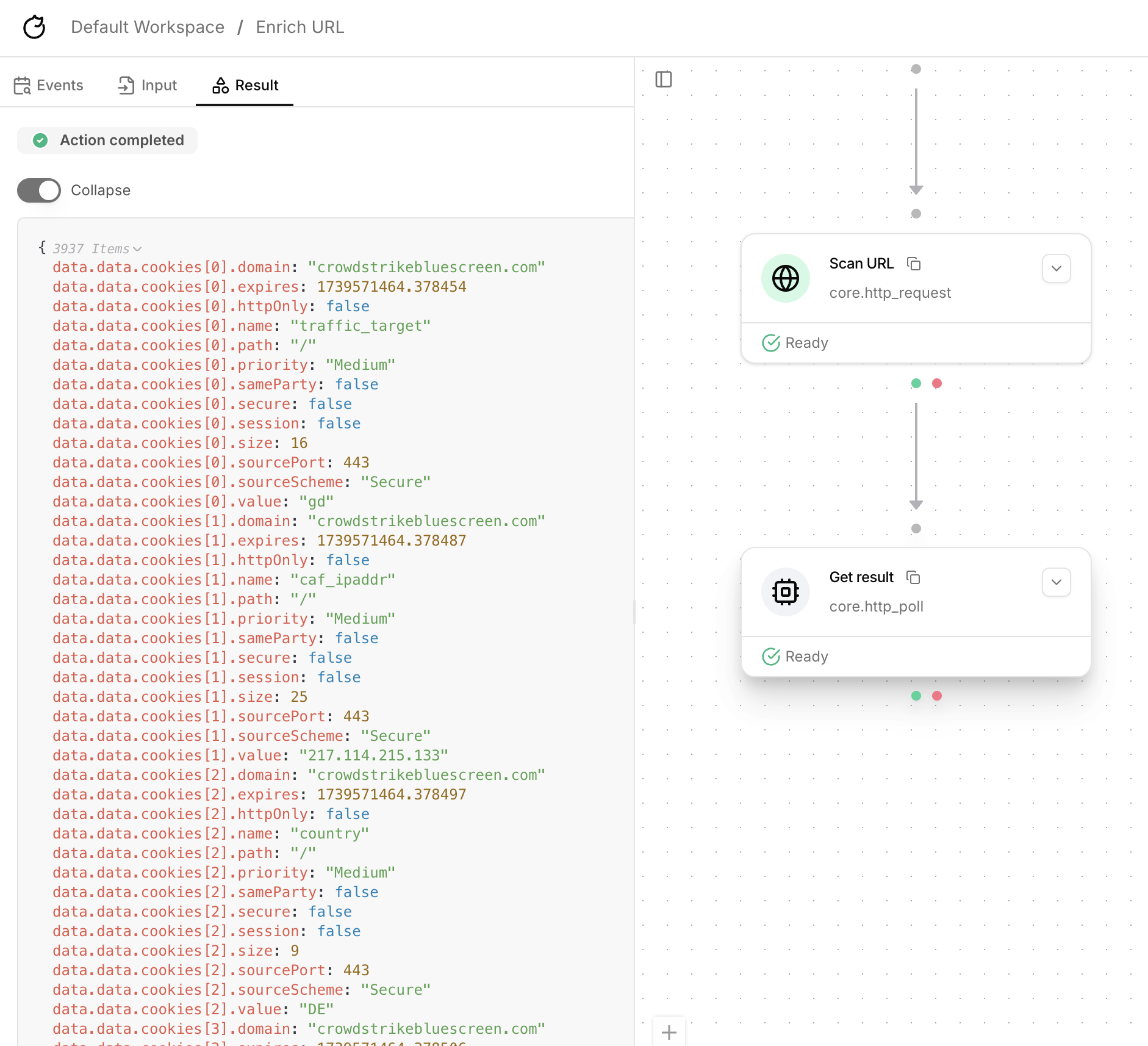
Poll /result endpoint
Add the 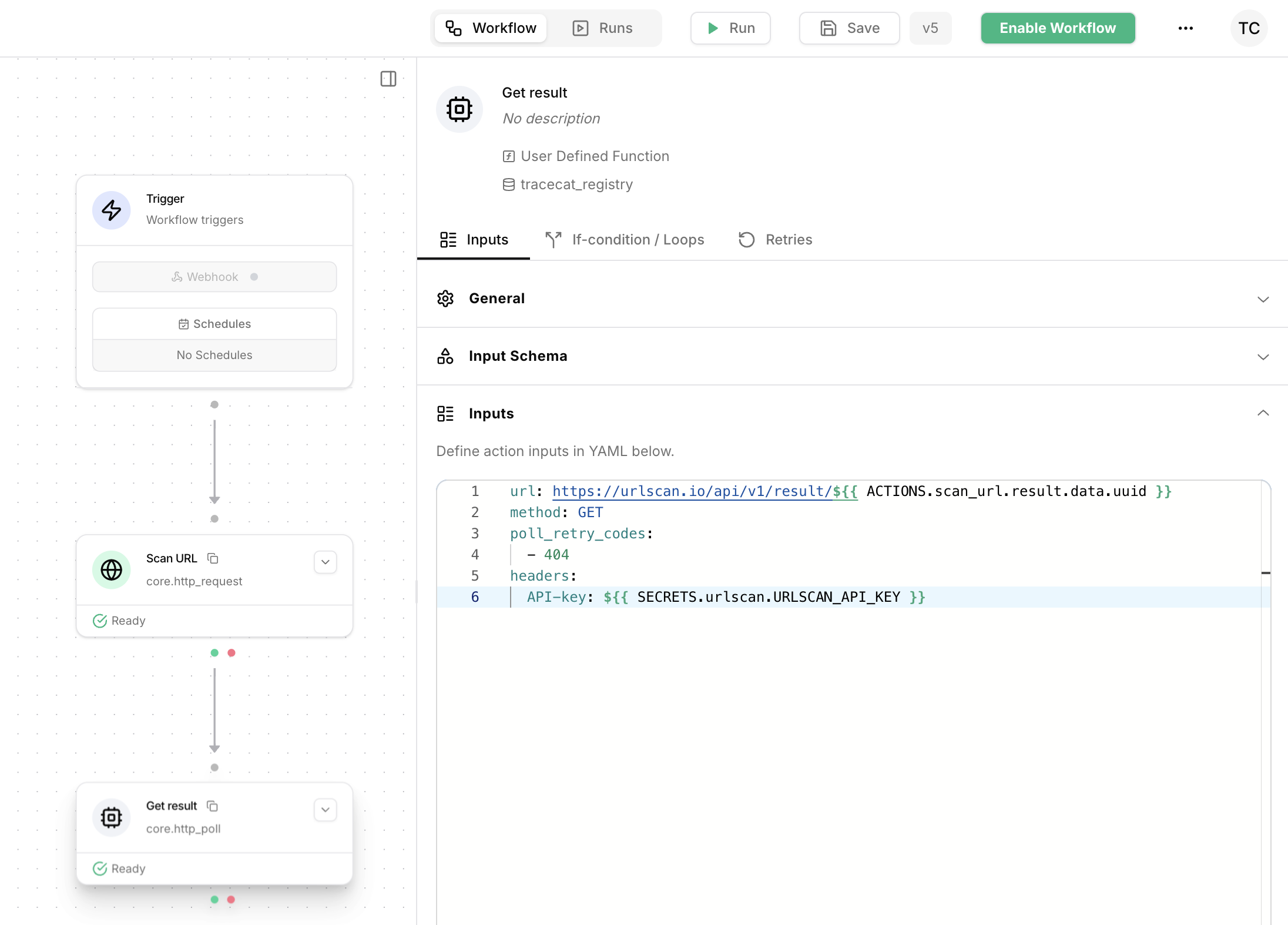
core.http_poll action to your workflow.
Rename it to Get result and configure it with the following inputs:
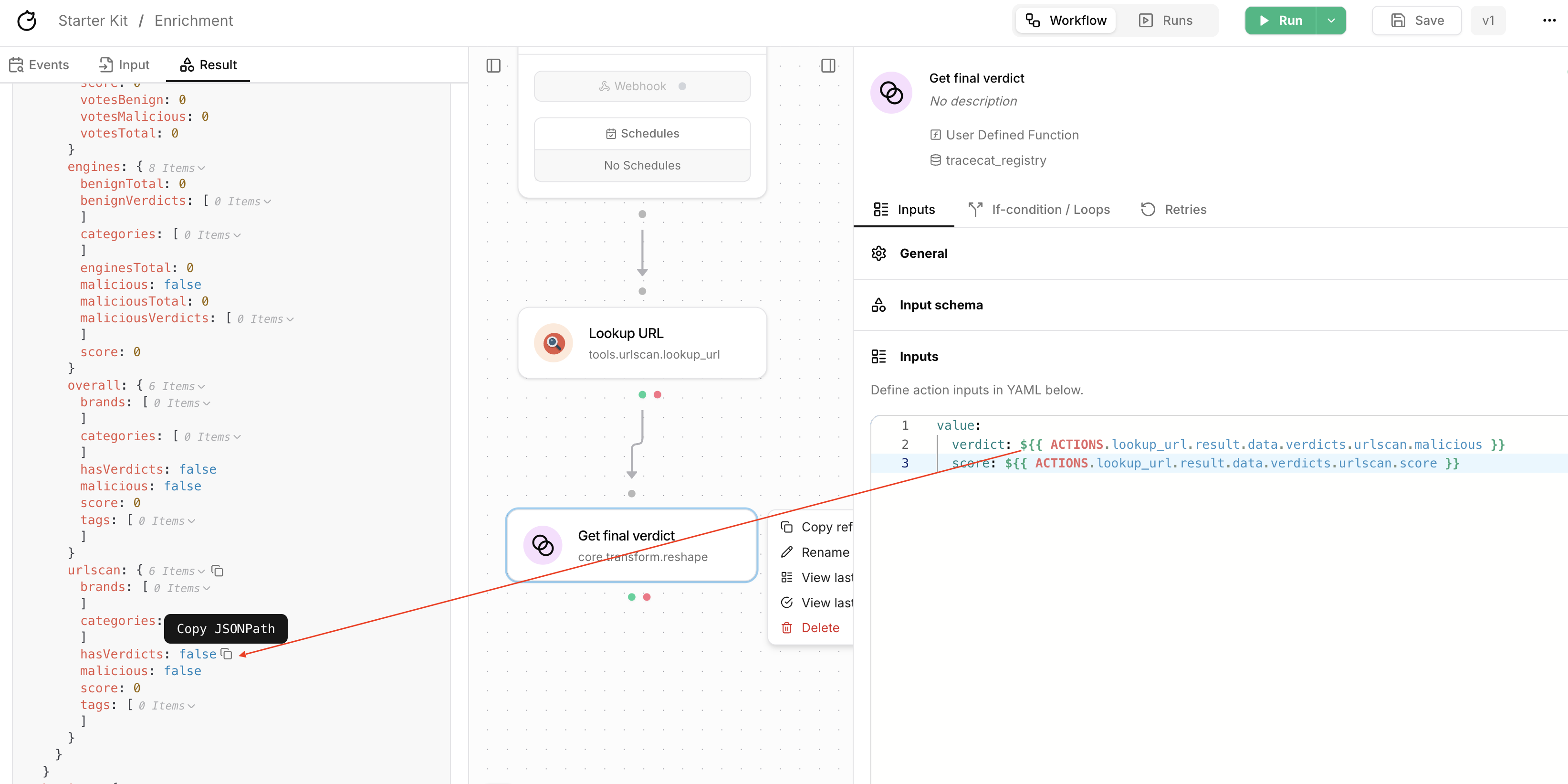
Get final verdict
Configure the reshape action to extract the maliciousness scores and categories from the response body.