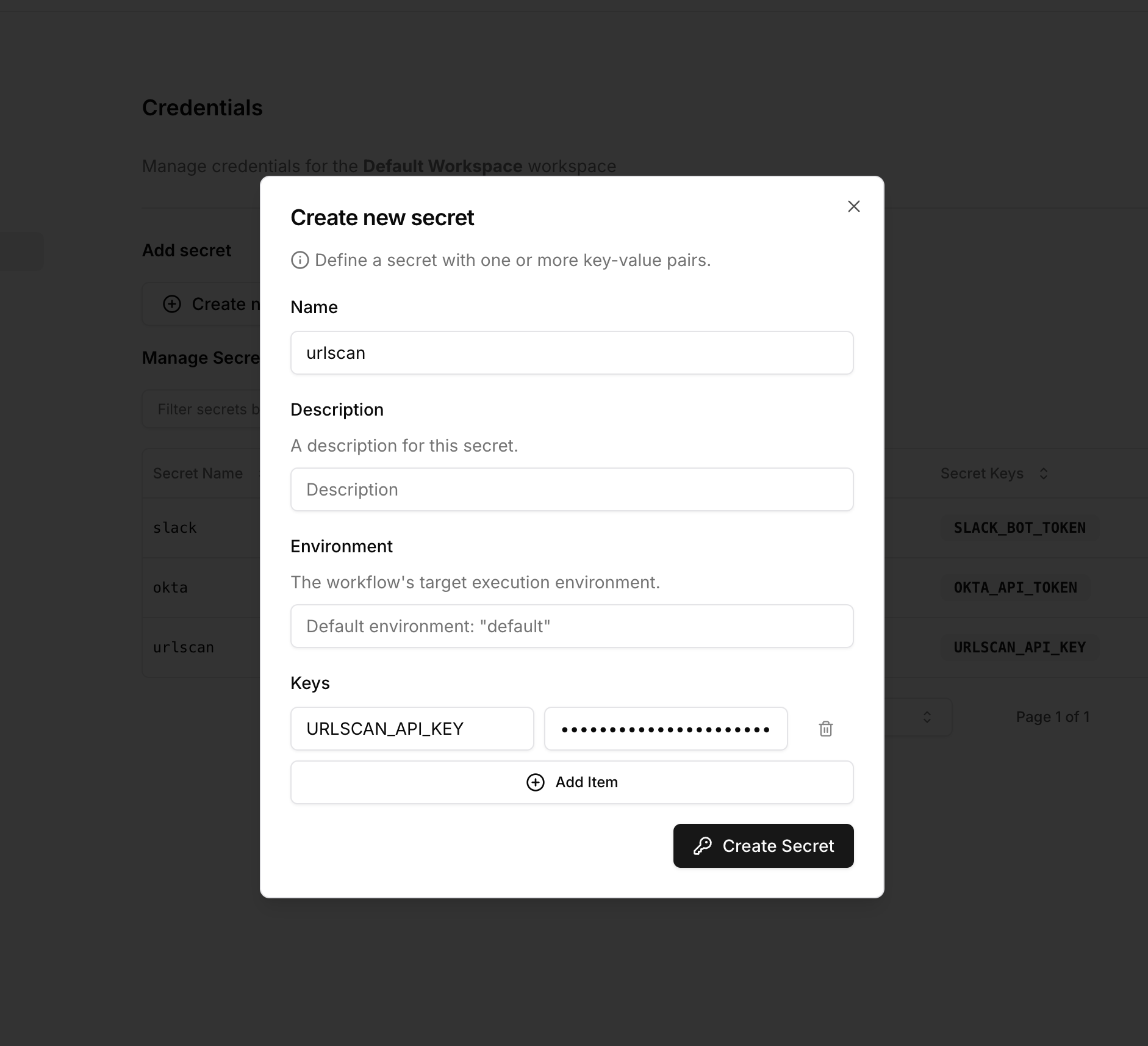
Storing secrets
Secrets are scoped to a workspace. To add a secret, navigate to the Credentials page and click on the Create Secret button.- Open credentials settings
- Create secret
Select the settings icon in the top right corner of the page and click on 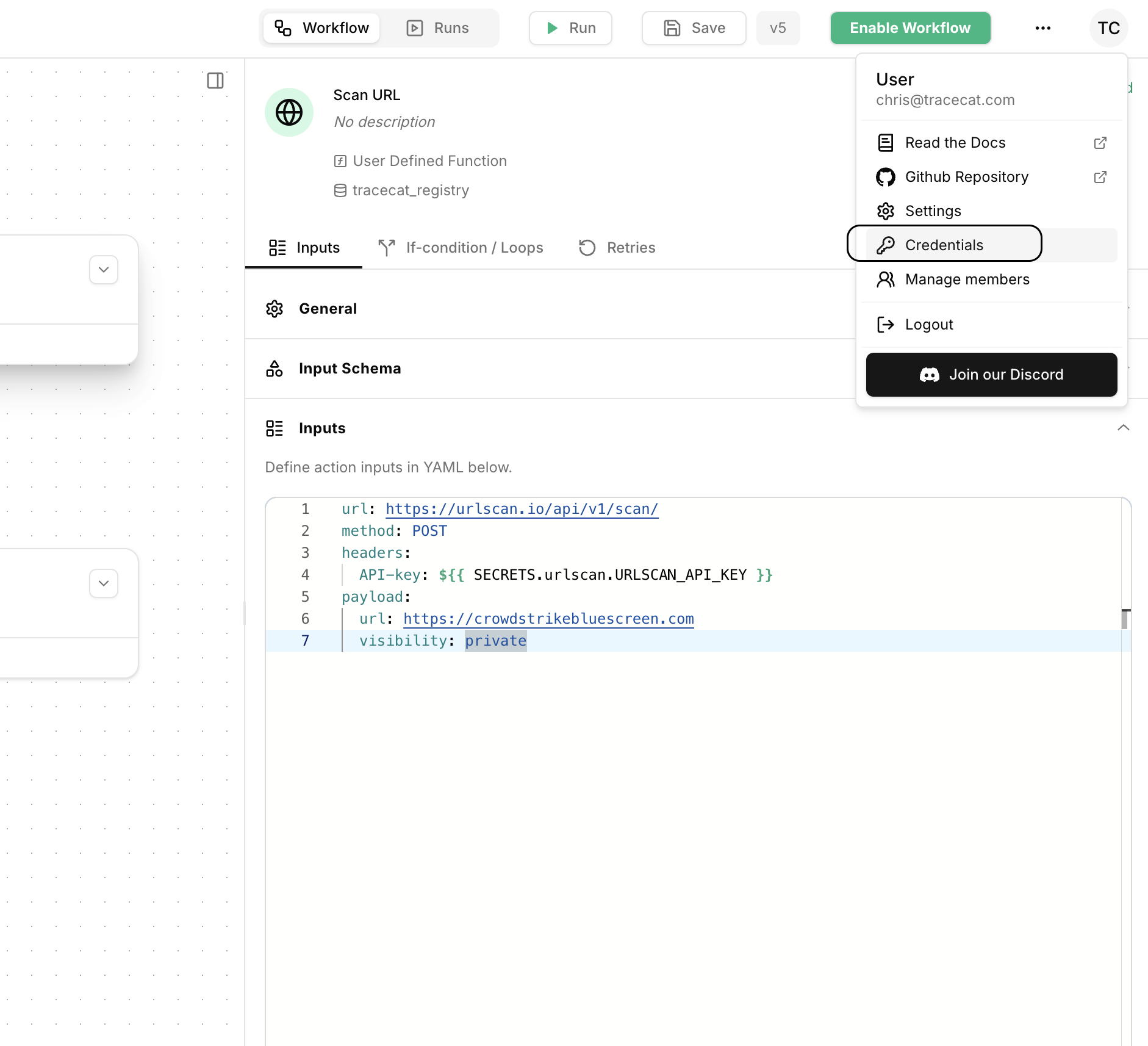
Credentials.
SECRETS context
Secrets stored in the secrets manager can be accessed using the SECRETS context: ${{ SECRETS.<name>.<key> }}.
For example:
Integrations and secrets
Authentication with pre-built integrations is handled implicitly. Pre-built integrations are associated with specific secret names and keys. For example, the VirusTotal integration requires a secret with the namevirustotal and the key VIRUSTOTAL_API_KEY.
Different integrations may require different required and optional keys.
For example, Tracecat’s AWS integration is configured with the following secret with optional keys, but with optional=False meaning at least one of the keys must be provided:
OAuth secrets
Unlike regular secrets, OAuth secrets are not stored in the secrets manager. Instead, they are stored in the OAuth provider’s database. To access them use the following syntax:<provider_id>is the OAuth provider identifier (e.g.,github,microsoft_teams)<PREFIX>is the provider ID in UPPERCASE (e.g.,GITHUB,MICROSOFT_TEAMS)- Use
USER_TOKENfor authorization code flow (delegated user access) - Use
SERVICE_TOKENfor client credentials flow (application access)
Custom OAuth providers
When you create a custom OAuth provider, the provider ID is automatically generated by:- Slugifying the name (lowercase, spaces replaced with underscores)
- Prepending the
custom_prefix
custom_my_custom_app.
To access tokens from custom OAuth providers:
| Provider Name | Provider ID | User Token Expression |
|---|---|---|
| My Custom App | custom_my_custom_app | ${{ SECRETS.custom_my_custom_app_oauth.CUSTOM_MY_CUSTOM_APP_USER_TOKEN }} |
| Acme API | custom_acme_api | ${{ SECRETS.custom_acme_api_oauth.CUSTOM_ACME_API_USER_TOKEN }} |
USER_TOKEN with SERVICE_TOKEN:
Multi-tenant secrets
A common use case is to have different sets of the same secret for different tenants. For example, an MDR provider will likely have different Crowdstrike tenant IDs for each customer. Tracecat supports multi-tenant secrets via the workflow’senvironment configuration.
Example
Create a multi-tenant secret
Create a multi-tenant secret for an integration by specifying the environment key.
The secret name and keys (e.g. 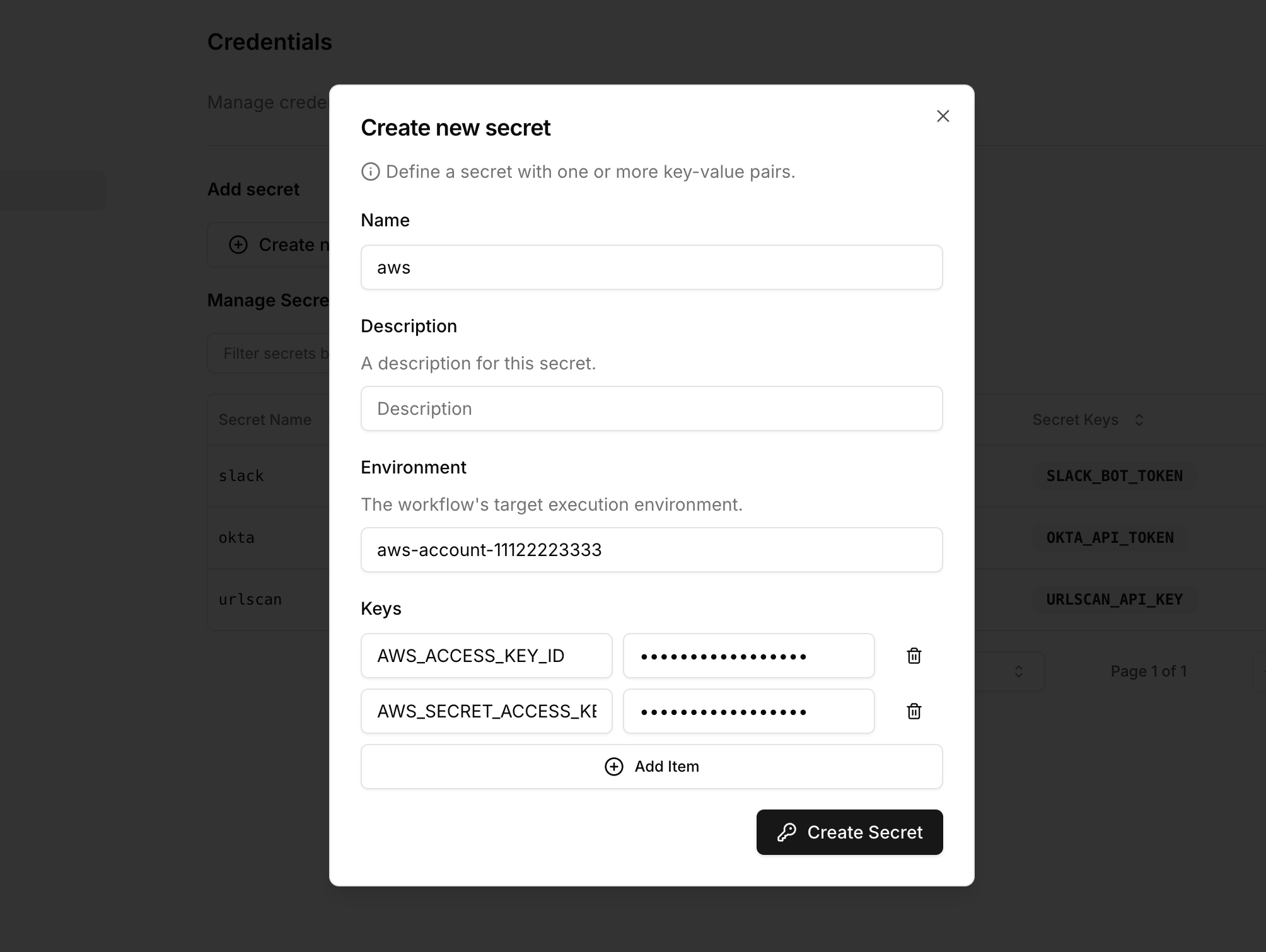
aws and AWS_ROLE_ARN) remain the same.If no environment key is specified, the environment key defaults to default.
Specify workflow environment
Click on the workflow canvas. You can specify the workflow’s environment under the 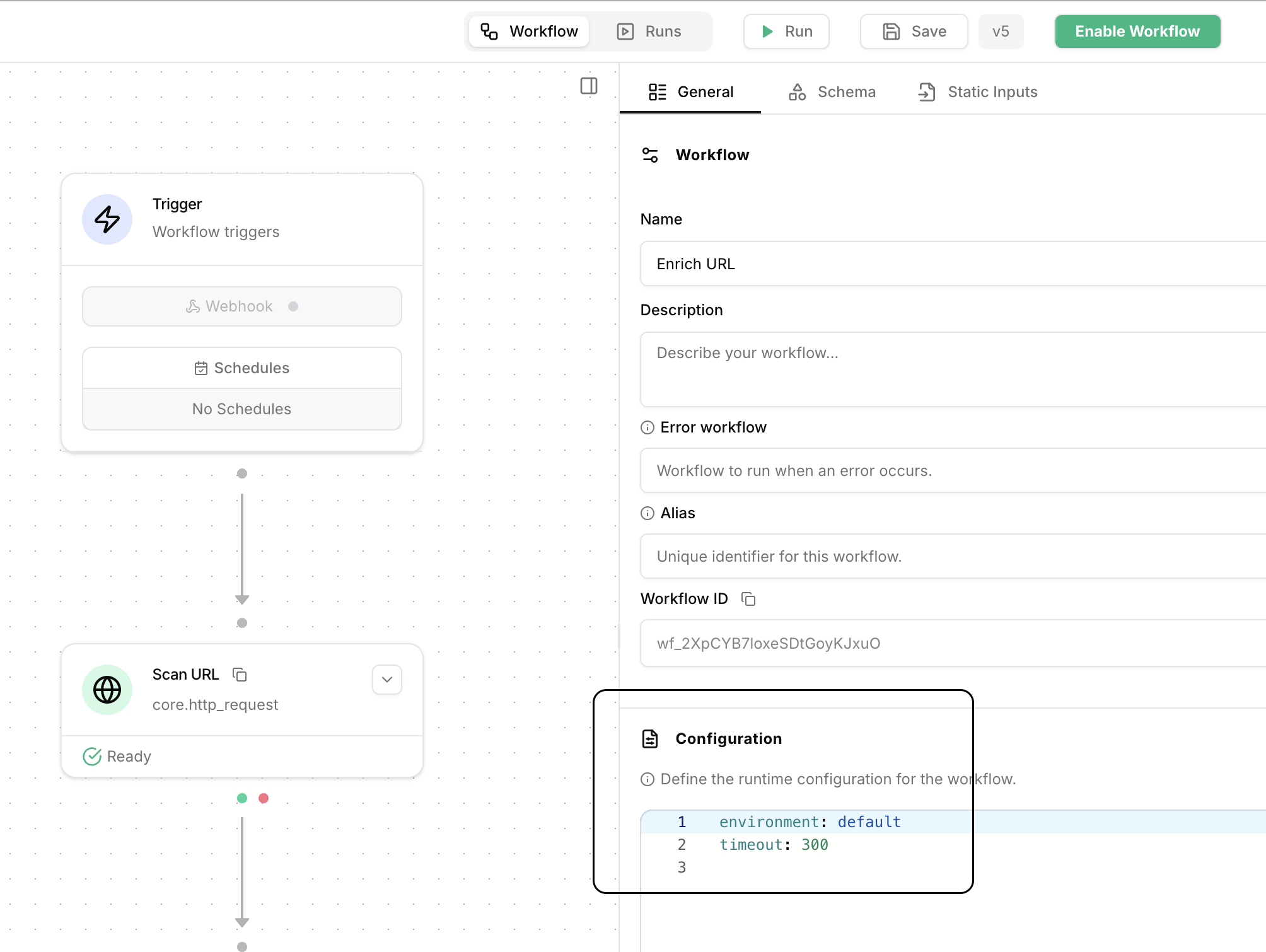
Configuration section.
Trigger multi-tenant workflows
Let’s say you have multiple sets of AWS credentials, one for each account, and you want to retrieve GuardDuty detections for each account.You can do this easily in two-steps using a looped 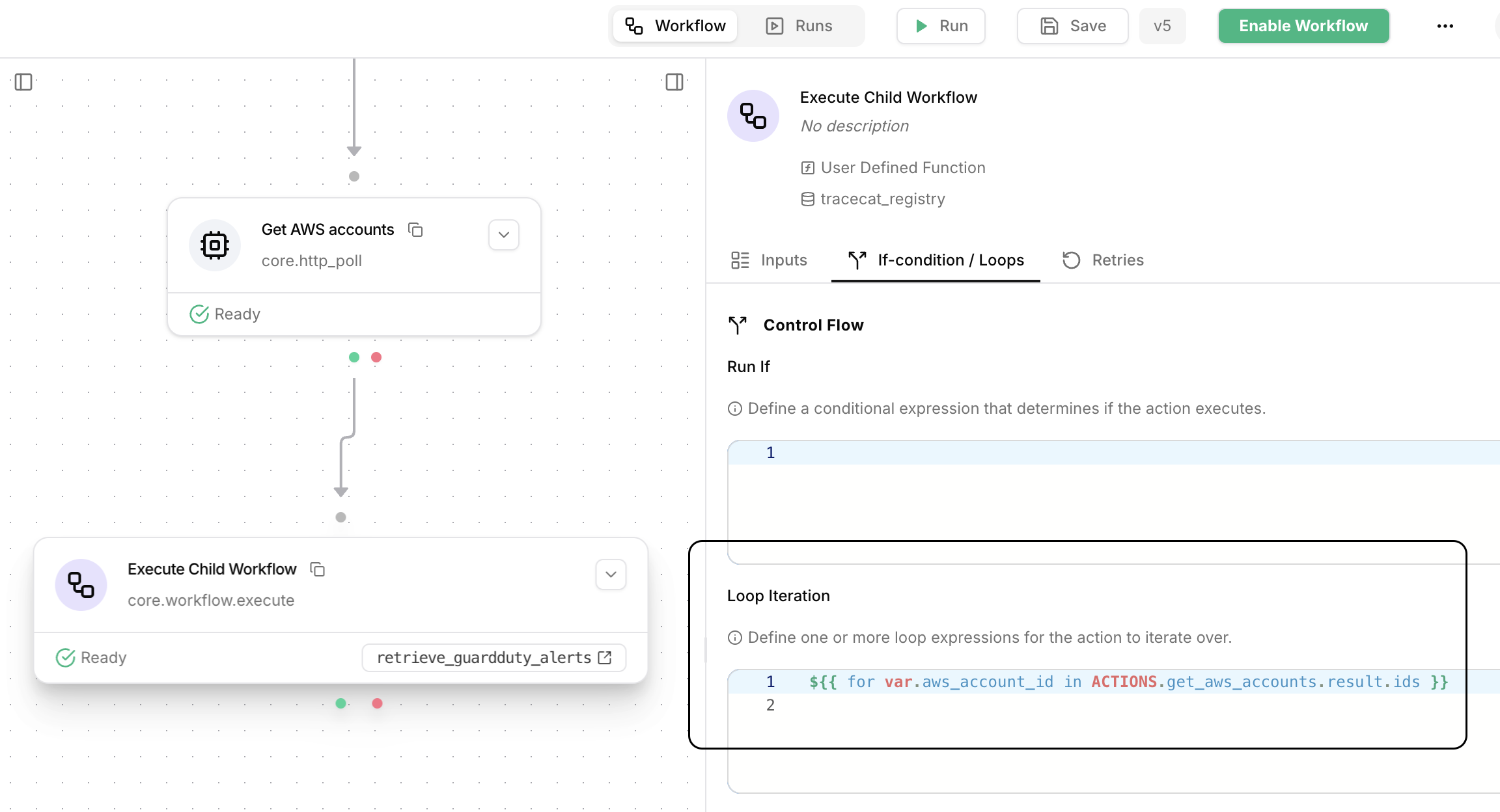
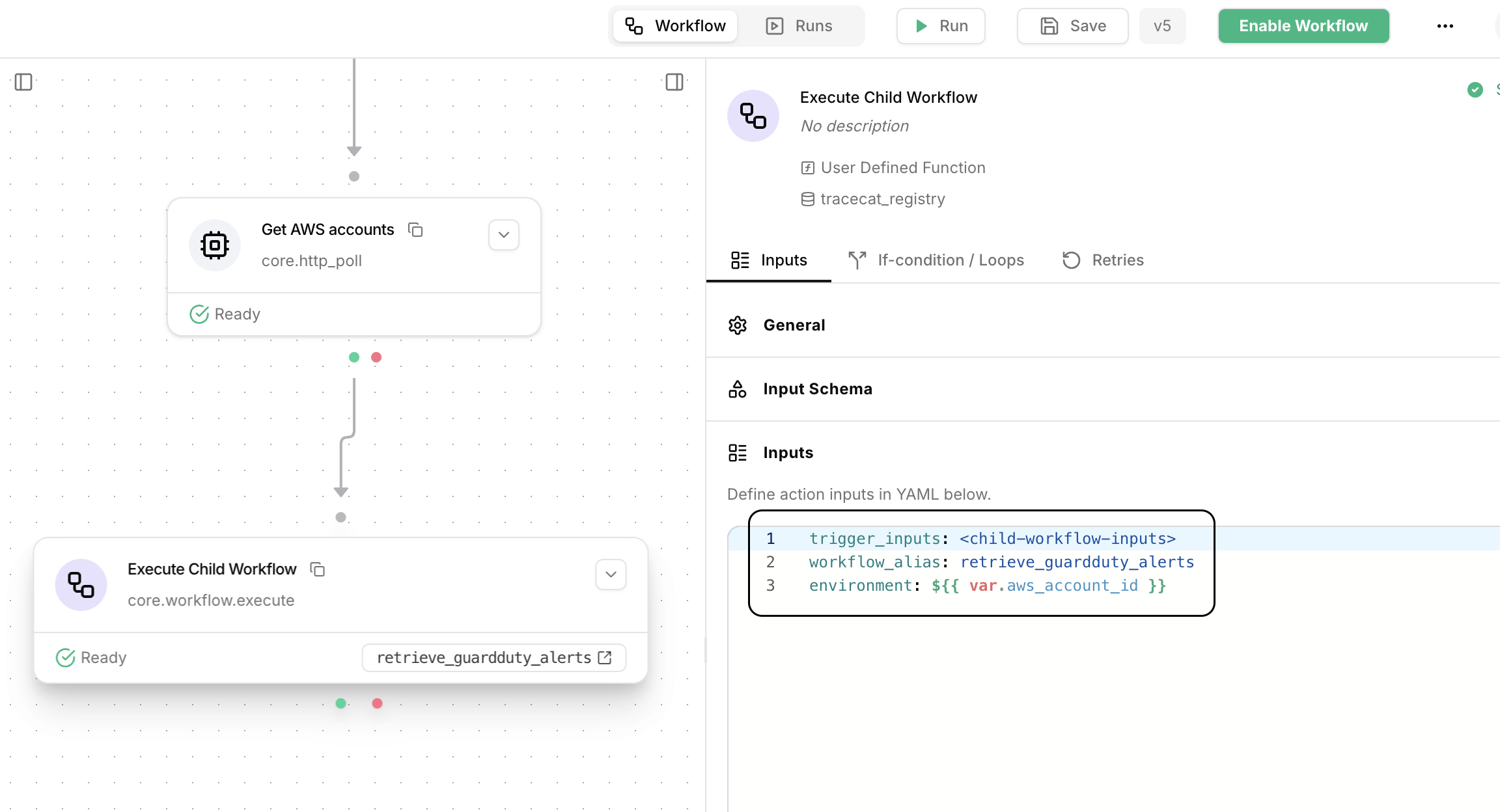
core.workflow.execute action.First, drag out a core.workflow.execute action, then specify a loop expression that iterates over a list of AWS account IDs:
core.workflow.execute action with the following inputs: